by Chirath De Alwis
Due to the rapid spread of internet use all over the world, email has become a primary communication medium for many official activities. Not only companies, but also members of the public tend to use emails in their critical business activities such as banking, sharing official messages, and sharing confidential files. However, this communication medium has also become vulnerable to attacks. This article focuses on email architecture and existing investigation techniques used by forensic investigators.
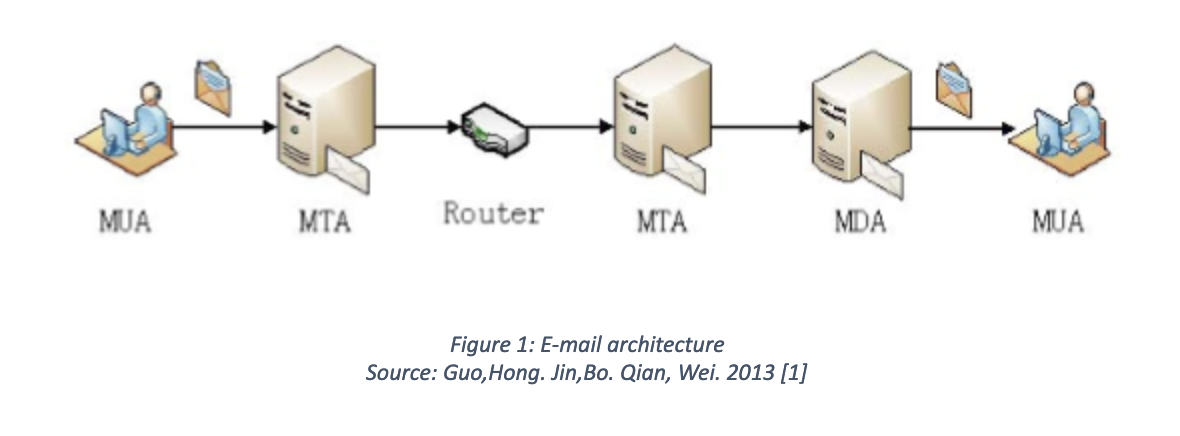
Email Architecture
When a user sends an email to a recipient, this email does not travel directly into the recipient’s mail server. Instead it passes through several servers. The MUA is the email program that is used to compose and read the email messages at the client end [1]. There are multiple MUAs available such as Outlook express, Gmail, and Lotus Notes. MTA is the server that receives the message sent from the MUA. Once the MTA receives a message it decodes the header information to determine where the message is going, and delivers the message to the corresponding MTA on the receiving machine [1]. Every time when the MTA receives the message, it modifies the header by adding data. When the last MTA receives the message, it decodes it and sends to the receiver’s MUA, so the message can then be seen by the recipient. Therefore an email header has multiple pieces of server information, including IP addresses.
Email Identities and Data
The primary evidence in email investigations is the email header. The email header contains a considerable amount of information about the email. Email header analysis should start from bottom to top, because the bottom-most information is the information from the sender, and the top-most information is about the receiver. In the previous section it was shown that email travels through multiple MTAs. These details can be found in the email header. The following picture depicts a sample header.
In order to understand the header information, it is necessary to understand the structured set of fields available in the header. The following are some of the basic field names and descriptions.
Email Forensic Investigation Techniques
Email forensics refers to analyzing the source and content of emails as evidence. Investigation of email related crimes and incidents involves various approaches.
Header Analysis
Email header analysis is the primary analytical technique. This involves analyzing metadata in the email header. It is evident that analyzing headers helps to identify the majority of email-related crimes. Email spoofing, phishing, spam, scams and even internal data leakages can be identified by analyzing the header.
Server Investigation
This involves investigating copies of delivered emails and server logs. In some organizations they do provide separate email boxes for their employees by having internal mail servers. In this case, investigation involves the extraction of the entire email box related to the case and the server logs.
Network Device Investigation
In some investigations, the investigator requires the logs maintained by the network devices such as routers, firewalls and switches to investigate the source of an email message. This is often a complex situation where the primary evidence is not percent (when the ISP or proxy does not maintain logs or lacks operation by ISP [2]).
Software Embedded Analysis
Some information about the sender of the email, attached files or documents may be included with the message by the email software used by the sender for composing the email [2]. This information may be included in the form of custom headers or in the form of MIME content as a Transport Neutral Encapsulation Format (TNEF)[2].
Sender Mail Fingerprints
The “Received” field includes tracking information generated by mail servers that have previously handled a message, in reverse order. The “X-Mailer” or “User-Agent” field helps to identify email software. Analyzing these fields helps to understand the software, and the version used by the sender.
Use of Email Trackers
In some situations, attackers use different techniques and locations to generate emails. In such situations it is important to find out the geographical location of the attacker. To get the exact location of the attacker, investigators often use email tracking software embedded into the body of an emaqil. When a recipient opens a message that has an email tracker attached, the investigator will be notified with the IP address and geographical location of the recipient. This technique is often used to identify suspects in murder or kidnapping cases, where the criminal communicates via email.
Volatile Memory Analysis
Recent research has been conducted in analyzing spoofed mails from volatile memory [3]. Since everything passes through volatile memory, it is possible to extract email related evidence (header information) from volatile memory.
Attachment Analysis
Most viruses and malware are sent through email attachments. Investigating attachments is crucial in any email-related investigation. Confidential information leakage is another important field of investigation. There are software tools available to recover email-related data, such as attachments from computer hard discs. For the analysis of suspicious attachments, investigators can upload documents into an online sandbox such as VirusTotal [4] to check whether the file is malware or not. However, it is important to bear in mind that even if a file passes a test such as VirusTotal’s, this is not a guarantee that it is fully safe. If this happens, it is a good idea to investigate the file further in a sandbox environment such as Cuckoo [5].
References
- Guo,Hong. Jin,Bo. Qian, Wei. 2013. [Online]. Analysis of Email Header for Forensics Purpose. Available from: https://ieeexplore.ieee.org/document/6524415?fbclid=IwAR2G2rRL_55D1D9N47deGryz6AJIxmFQ7eC1HCIvei_-VgJi2DMSjHMzau8. [Accessed:02/14/2019]
- Banday.M.T. 2011. [Online]. TECHNIQUES AND TOOLS FOR FORENSIC INVESTIGATION OF EMAIL. Available from: https://pdfs.semanticscholar.org/8625/a3b17d199e5cabbb796bad0df56a7979c77c.pdf. [Accessed:02/14/2019]
- Iyer.R.P, et la.2017. Email spoofing detection using volatile memory forensics. [Online]. Available from: https://ieeexplore.ieee.org/document/8228692. [Accessed:02/14/2019]
- VirusTotal. 2019. [Online]. Available from: https://www.virustotal.com/. [Accessed:02/14/2019]
- Cuckoosandbox. 2019. [Online]. Available from: https://cuckoosandbox.org/. [Accessed:02/14/2019]
About The Author
 Chirath De Alwis is an information security professional with more than four years’ experience in Information Security domain. He holds BEng (Hons), PGdip and eight professional certifications in cyber security and also reading for his MSc specializing in Cyber Security. Currently, Chirath is involved in vulnerability management, Threat Intelligence, incident handling and digital forensics activities in Sri Lankan cyberspace. You can contact him on chirathdealwis@gmail.com.
Chirath De Alwis is an information security professional with more than four years’ experience in Information Security domain. He holds BEng (Hons), PGdip and eight professional certifications in cyber security and also reading for his MSc specializing in Cyber Security. Currently, Chirath is involved in vulnerability management, Threat Intelligence, incident handling and digital forensics activities in Sri Lankan cyberspace. You can contact him on chirathdealwis@gmail.com.