Almost everyone who uses the Internet has a web-based email account. Many people have two or more, so the likelihood of a forensic investigator coming across a case involving webmail communication is very high. While law enforcement examiners can ask service providers for the email contents through a court order, corporate and non-government examiners have to rely on what evidence is left on the computer or mobile device.
The three largest webmail providers are Google’s Gmail, Microsoft’s Hotmail/Outlook.com, and Yahoo Mail. Together they account for well over one billion users. Each provider offers some unique features but they’re generally all quite similar in implementation from a forensics standpoint. This article will discuss how webmail artifacts are stored and investigated on a PC or laptop, mobile devices, and other applications that support and store webmail evidence.
Browsers
On a PC, most webmail activity is conducted through the browser so it’s no surprise that the majority of your evidence will consist of browser artifacts. Depending on the browser used, the data will be stored differently but typically the cache, history, and cookies are your best sources of evidence. History and cookies will provide dates, times, and sites visited but the data of real evidentiary value is found in the cache. The cache stores web page components to the local disk to speed up future visits. Many emails read by the suspect are found in the cache folders and those locations vary depending on the operating system and browser used.
Internet Explorer
Since Internet Explorer (IE) is installed by default on most Windows installations, it’s likely the most commonly used and should always be searched when looking for webmail—or any browsing artifacts for that matter. Depending on the version of Windows and IE installed, the evidence will be stored in different locations. The locations are listed below:
- WinXP – %root%/Documents and Settings/%userprofile%/Local Settings/Temporary Internet Files/Content.IE5
- Win Vista/7 – %root%/Users/%userprofile%/AppData/Local/Microsoft/Windows/Temporary Internet Files/Content.IE5
- Win Vista/7 – %root%/Users/%userprofile%/AppData/Local/Microsoft/Windows/Temporary Internet
- Files/Low/Content.IE5
- Win8/IE10 – %root%/Users/%userprofile%/AppData/Local/Microsoft/Windows/History
Note: Internet Explorer 10 is available on Windows 7 as well. If IE9 was installed and then upgraded to IE10, there will be two sources of evidence (the index.dat file from IE9 and the database within the webcache folder for IE10).
Mozilla Firefox
Firefox is a very popular browser and also stores its cache data in various locations based on the operating system installed. It’s installed as the default browser on many Linux distributions and is available for MacOS-X as well.
- WinXP – %root%/Documents and Settings/%userprofile%/Local Settings/Application Data/Mozilla/Firefox/Profiles/*.default/Cache
- Win7/8 – %root%/Users/%userprofile%/AppData/Local/Mozilla/Firefox/Profiles/*.default/Cache
- Linux – /home/%userprofile%/.mozilla/firefox/$PROFILE.default/Cache
- MacOS-X – /Users/%userprofile%/Library/Caches/Firefox/Profiles/$PROFILE.default/Cache/
Google Chrome
Google Chrome is also one of the top 3 browsers used today. It is available for Windows, Linux, and MacOS-X. Google also makes the Chromium open source project available to Linux users and runs very similar to the regular Chrome package with some minor differences i.
- WinXP – %root%/Documents and Settings/%userprofile%/Local Settings/Application Data/Google/Chrome/User Data/Default/Cache
- Win7/8 – %root%/Users/%userprofile%/AppData/Local/Google/Chrome/User Data/Default/Cache
- Linux – /home/%userprofile%/.config/google-chrome/Default/Application Cache/Cache/
- MacOS-X – /Users/%userprofile%/Caches/Google/Chrome/Default/Cache/
While the other browsing artifacts will show evidence of visiting the site, the cache folders will show the actual contents of the page or message, which is significantly more important when dealing with webmail artifacts. One caveat to mention is that typically you won’t find a cached page of any messages sent (only read) by the suspect since the message is typed on screen and then sent by the user without actually viewing the message outside of the text box or script. The only time the sent messages are cached is when the suspect views the HTML message in the “Sent Messages” folder after sending.
It is important to note that these will not be the only places to search for webmail artifacts. System memory/pagefile.sys are sometimes the only place to find webmail artifacts such as Gmail, and volume shadow copies/restore points, and hibernation files, all contain valuable historical data that can be used in conjunction with the evidence found in the areas above.
While the cached pages can be manually parsed and viewed using traditional forensics tools, Magnet Forensics‘ Internet Evidence Finder™ (IEF) will automatically pull the relevant browsing data from all the common browsers that a suspect might have used and sort it into specific categories based on the webmail service provider. They can then be viewed within the report viewer for quick and easy analysis.

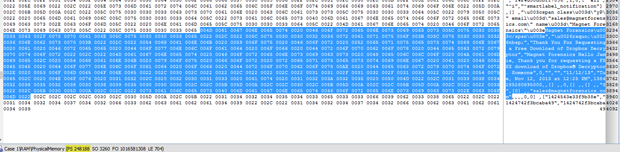
In the example below we have found Gmail fragments in memory at physical sector 248188 using EnCase. All the data is there but as memory is typically a sector level search, it is not easily searched or organized.
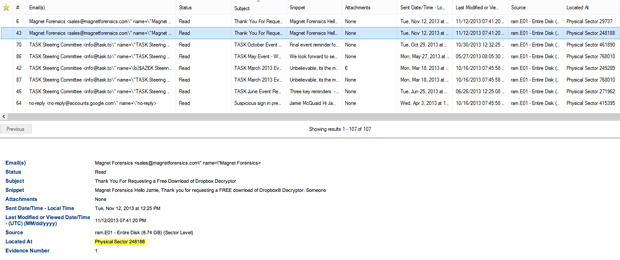
Once the image or drive is analyzed with IEF, Report Viewer will sort any evidence found by the service provider. IEF then automatically parses the sender/receiver details, the subject, and the date of the message into columns for fast sorting and then displays the contents of the message in the window below. With the same data we used in our EnCase example, IEF has analyzed the evidence and pulled all the relevant data into Report Viewer for easier searching.
Review of the relevant artifacts reveals not only browser artifacts of the messages that were opened by the user but IEF also parses many of the emails that were not opened by the suspect and simply displayed by the inbox or folder view of the webmail in the browser. Many times this type of information can be found in memory, pagefile.sys, or hiberfil.sys. Since the message in this example wasn’t opened by the user during the given browsing session, IEF is unable to show the contents of the message in this circumstance, however it will give a better picture of what resided in the user’s inbox at the time of viewing.
Overall, webmail artifacts are an important part of many investigations. Either as a primary source of information or as corroborating evidence, webmail can be found in the browser artifacts or memory of most PCs or laptops.
What about other sources of webmail evidence?
Forensic investigations have moved beyond just desktop PCs or laptops since most people now access email from their mobile devices as well. What started out as a tool for only the most serious business person has now spread to even the most casual consumer. IEF is able to analyze email found on the two most commonly used platforms, Android and iOS.
There are many forensic tools that specialize in mobile acquisitions. Cellebrite, XRY, and Oxygen are excellent resources to acquire the large variety of mobile devices and connectors. Much like previous versions of IEF, IEF Advanced focuses on the analysis of the acquired data and leaves the imaging to the other tools. Once the image is acquired, IEF will analyze all of the common outputs from the mobile acquisition tools (dd, raw, img, bin, 001, ima, vfd, flp, bif) as well as all the EnCase formats (E01, L01, Ex01, Lx01).
Focusing on the analysis allows IEF to specialize in the artifacts that are found within an image and produce the best results whether the evidence is found on a suspect’s PC or mobile device.
IEF can handle both physical and logical mobile images for iOS and Android, but a physical image is always preferable when possible in order to carve out deleted artifacts stored in unallocated space. If a logical image is acquired, unallocated space is not captured and therefore cannot be searched.
Android/iOS Mailbox, Gmail Application
Emails are handled differently on a mobile device than webmail is on a traditional PC. Typically on a PC, webmail is handled through the browser, and most of the evidence is found in browser artifacts or memory. Howerver, with mobile devices, there is typically a native mailbox application for all of a user’s email accounts, whether they are webmail or server based.
For iOS the native mailbox is stored as a SQLite database here:
/private/var/mobile/Library/Mail/Protected Index and Envelope Index
For Android it is also stored as a SQLite database here:
/data/data/com.google.android.email/databases/EmailProvider.db
IEF is able to parse and carve the native email clients for both iOS and Android devices by accessing the SQLite database that stores the messages and structures the sender/recipients, CC/BCC, date/time, subject, status, message content, and attachment for each message recovered from the native application into the IEF Report Viewer.
Email can also be stored in a dedicated application if one exists, as is the case with Gmail.

Many mobile devices have a dedicated mail application for Gmail or other popular webmail accounts. This provides users with enhanced features available to Gmail based webmail that might not be available if the native mailbox is used.
The Gmail application is stored as a SQLite database for Android devices here:
/data/data/com.google.android.gm/databases/mailstore.%GmailUserID%@gmail.com.db
In addition, make sure to search the mobile browser activity for additional webmail that may have been accessed through the browser and wasn’t setup in either the native or custom mailbox application, such as the Gmail app.
Webmail has extended far beyond the traditional browser and your investigation should as well. With mobile database applications storing messages from multiple webmail accounts and new application artifacts being created regularly, it is difficult for an investigator to know where to look for all potential evidence, let alone have the time to search everywhere for each case. Tools such as IEF expedite that process greatly and help investigators understand the bigger picture when it comes to Internet evidence—and the number applications that store the evidence only continues to grow.
*For more detail on Chromium and its differences, see:
https://code.google.com/p/chromium/wiki/ChromiumBrowserVsGoogleChrome
As always, please let me know if you have any questions, suggestions or requests. I can be reached by email at jamie.mcquaid(at)magnetforensics(dot)com.
Jamie McQuaid
Forensics Consultant, Magnet Forensics